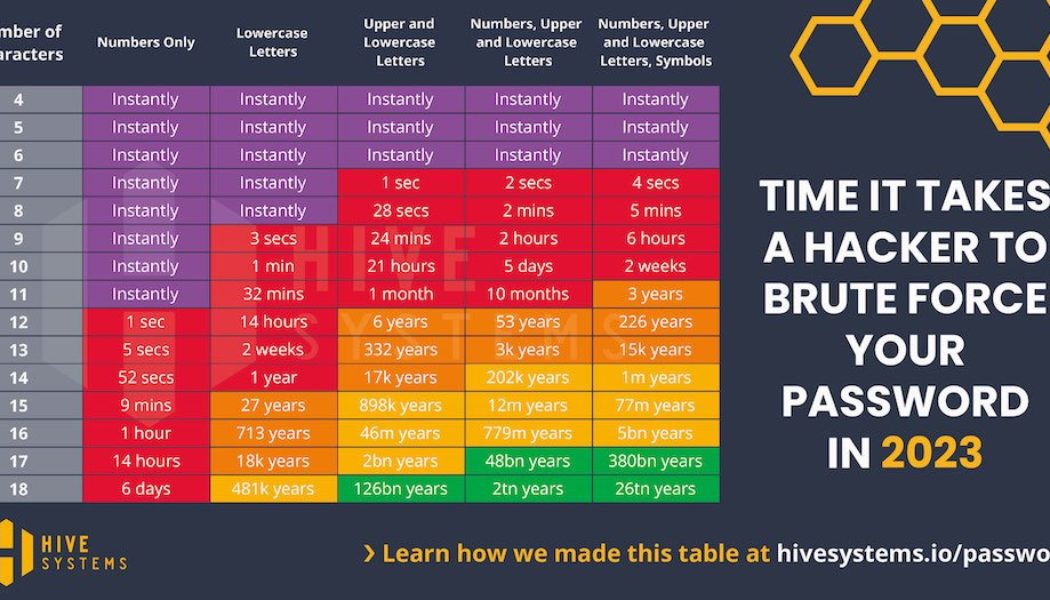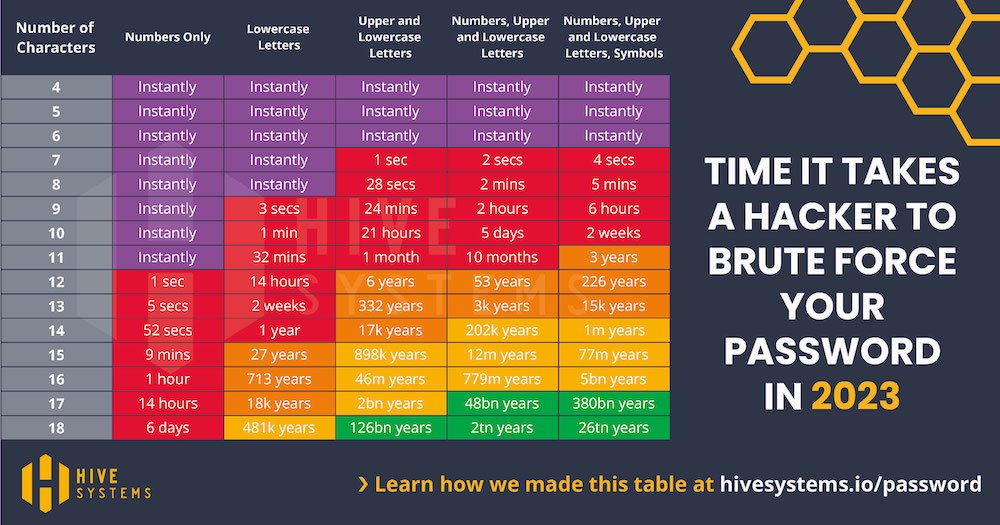
Since 2020, we’ve conducted a lot of research to develop and present the Hive Systems Password Table. But for those of you that want to know about the “how” then you’ve come to the right place because we’re going to walk you through our methodology. While the data fits nicely into the table above, things aren’t as as simple as they look. So we’ll talk through the data, our assumptions, and oh, you’re going to see a LOT of variations of the password table.
Got a question or comment? Leave it below or message us on your favorite social media platform.
“So how’d you make the table”?”
In 2022, we shared our update to a colorful infographic table that showed the relative strength of a hashed password against a cracking attempt, based on the password’s length, complexity, hashing algorithm used by the victim, and the hardware used by the attacker. The data was based on how long it would take a consumer-budget hacker to crack your password hash using a desktop computer with a top-tier graphics card and then how long an organized-crime-budget hacker would take leveraging cloud compute resources. We looked at big name providers like Amazon AWS and Microsoft Azure but also the growing non-corporate options where you can rent a person’s computer at cost per hour.
This year we’ve updated our cracking hardware to the latest and greatest, including that of the internet darling ChatGPT! We also opted for a more realistic set of special characters in our testing. Most websites only accept these ^*%$!&@# and so we dropped the rest. This only impacts the right-most column of the password table.
First, let’s get some key terms out of the way. We’re going to talk about “hashing.” In the context of passwords, a “hash” is a scrambled version of text that is reproducible if you know what hash software was used. In other words, if your friend hashes the word “password” using MD5 hashing software, the output hash will be 5f4dcc3b5aa765d61d8327deb882cf99. Now if you hash the word “password” using MD5 hashing software, you’ll also get 5f4dcc3b5aa765d61d8327deb882cf99! You and your friend both secretly know the word “password” is the secret code, but anyone else watching you just sees 5f4dcc3b5aa765d61d8327deb882cf99. Passwords are stored in servers as hashes like this instead of in plain text like “password.” That way, if someone steals the database all they can see are these hashes but not the password that made them.
You can’t do the reverse. A hash digest like 5f4dcc3b5aa765d61d8327deb882cf99 can’t be computed to produce the word “password” that was used to make it. Hashing software is a one-way-street by design. The way that hackers solve this problem is by “cracking” the passwords instead. In this context, “cracking” means making a list of all combinations of characters on your keyboard and then hashing them. Then you look for matches between the list and a breached database of password hashes. You can do that with any computer, but it is much faster if you accelerate the process with a powerful graphics card.
Graphics cards are those circuit boards that stick out of your computer’s bigger green circuit board. Among other things, this special circuit board has a GPU on it. A GPU is the shiny square tile on your graphics card that says NVIDIA or AMD on it. GPU stands for graphical processing unit – they were built to make pictures load faster on your computer screen (and to play great video games). As it turns out, they’re also great at calculating hashes too. A popular application for hashing is called Hashcat. Hashcat includes hashing software like MD5 and allows you to try not just MD5 but thousands of others and see how fast it was able to do so. We usually say “hash function” instead of “hash software.”